23 September 2021
OWASP TOP 10 vulnerabilities – what’s new in the world of cybersecurity? The OWASP 2020 ranking is here!
The OWASP TOP 10 is one of the most famous industry rankings of web application security risks. In recent weeks, the long-awaited OWASP TOP 10 2020 version, which covers the years 2017-2020, finally showed up. Let’s take a look at the ranking itself and find out how many of our last year’s predictions made it to the list!
* The article has been recently updated to reflect the latest changes – the release of the OWASP TOP 10 2020 ranking. If you want to read just the latest update, use the “Contents” menu in the left sidebar to jump to the “OWASP TOP 10 2020 update” section or use this link.
Three years have passed since the last edition of the OWASP TOP 10 report. In cybersecurity, it’s practically an era. A lot has changed – new frameworks, versions, solutions and vulnerabilities and much more made their way to this dynamically changing world.
This year, we’re expecting to get the latest list of most popular vulnerabilities from the years 2017-2020 – the OWASP TOP 10 2020. Before it happens, let’s shed some light on what the OWASP organization is, how the ranking works and what the 2017 TOP 10 looked like. I’m also going to make predictions about the upcoming edition.
What is OWASP TOP 10?
The Open Web Application Security Project® (OWASP) is a nonprofit foundation that works to improve the security of software.
Through community-led open-source software projects, hundreds of local chapters worldwide, tens of thousands of members, and leading educational and training conferences, the OWASP Foundation is the source for developers and technologists to secure the web.
OWASP TOP 10 2017
The 2017 edition of the OWASP TOP 10 vulnerabilities ranking may be somewhat old, but it’s still the latest available version of it. Surely, it still holds some value.
The list of OWASP TOP 10 vulnerabilities included in the ranking is as follows:
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting (XSS)
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
Let’s take a closer look at each of them.
Injection
This category includes SQLi, NoSQLi, OS or LDAP injections. The first two refer to attempts to steal data from SQL/NoSQL databases. If your project is vulnerable, the user may be able to extract some valuable data such as email addresses, user and system data, passwords or logins.
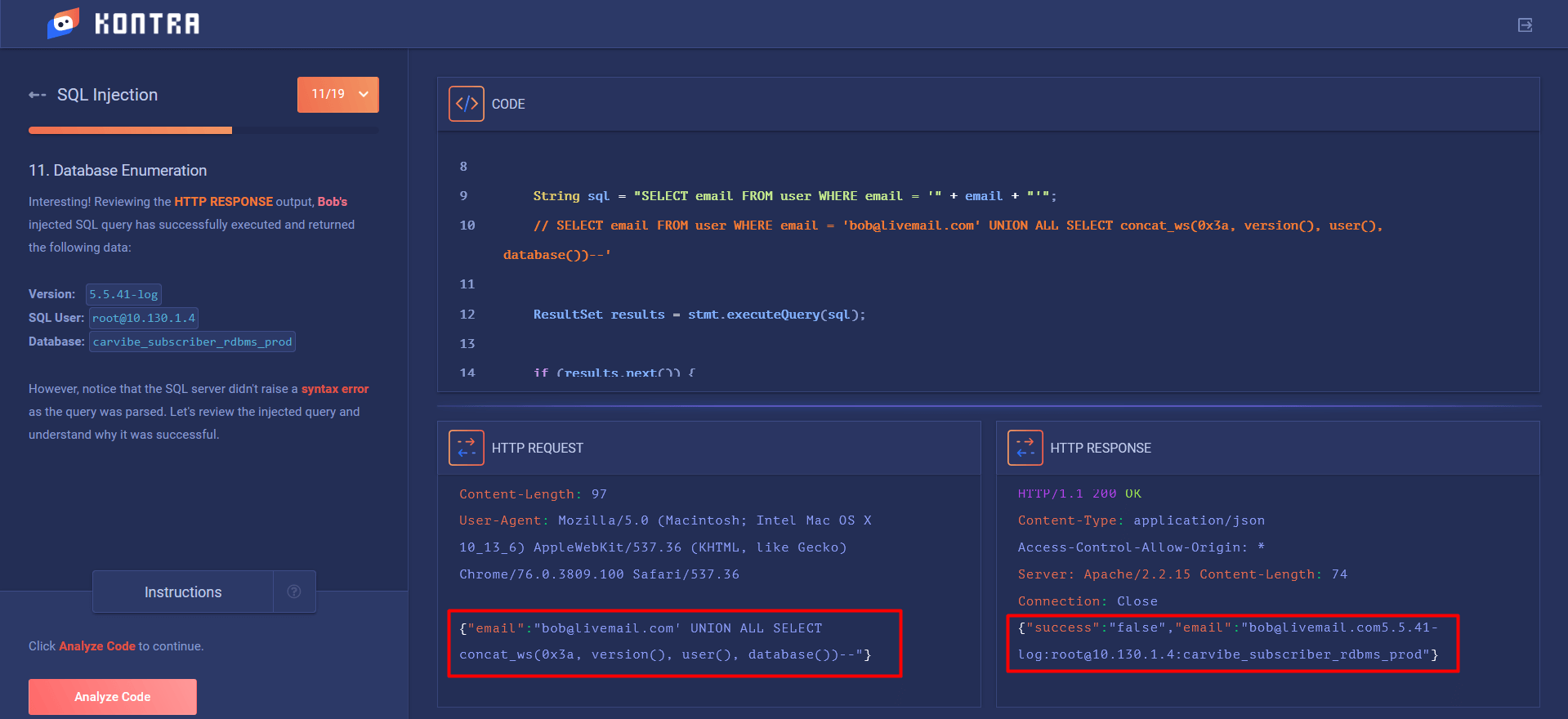
The OS injection makes it possible for the attacker to issue all kinds of system commands. It might cause all the security measures to fail. LDAP is a protocol for accessing and maintaining information services via the TCP/IP protocol. It’s designed for use with directory services, that is object databases that represent network users and resources. The attack involves using LDAP expressions to extract valuable data or to change access rights.
Broken Authentication
This one has to do with authentication and session management. The attacker’s goal is to compromise passwords, keys and session tokens as well as to exploit app errors in order to take over accounts of other users.
Common methods used to achieve it are brute force attacks and exploiting various weaknesses within the system such as poor password policy and management or weak session cookies. When the attack succeeds, the implications can be quite far-reaching, including leaking of personal data. The best ways to prevent it involve setting strong passwords, implementing multi-factor authentication, blocking users that fail to log in properly in a given number of attempts, session management testing/debugging, best by a dedicated Quality Assurance team.
Sensitive Data Exposure
Nowadays it’s extremely important to take care of the user’s personal and financial data. Otherwise, Sensitive Data Exposure may happen and not only will you stand to compromise the application, but earn yourself a hefty fine in the process (read more about the GDPR). The Sensitive Data Exposure vulnerability is becoming increasingly relevant to the everyday reality of each online business.
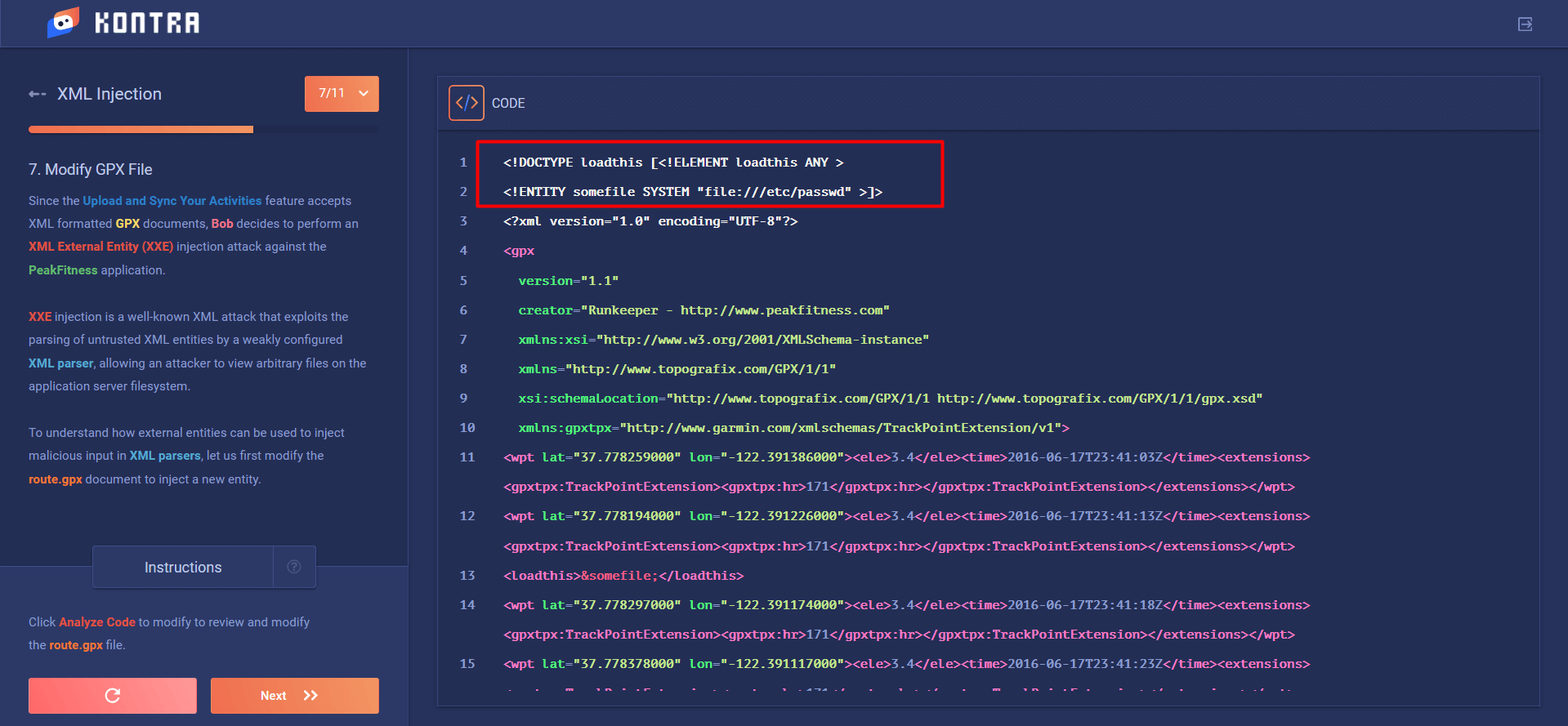
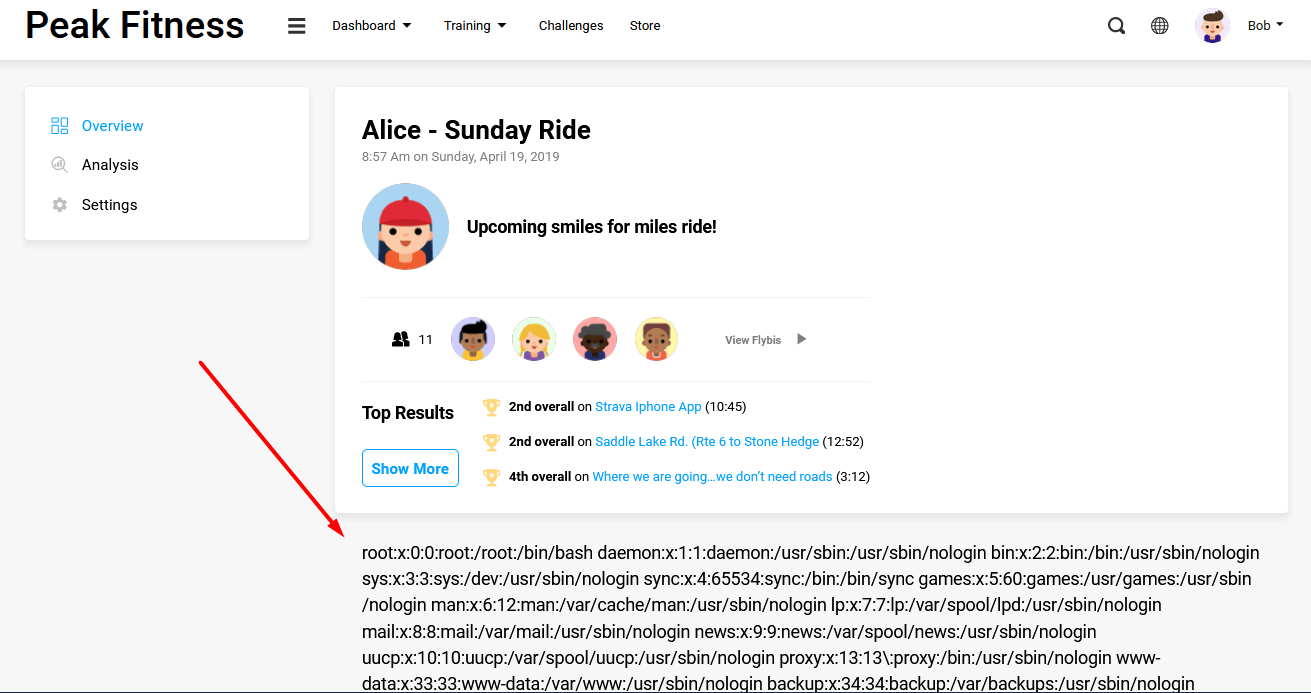
XML External Entities (XXE)
This category refers to abusing features of XML parsers. Such vulnerabilities may also cause Denial of Service (DoS) or Server Side Request Forgery (SSRF) attacks, which can in turn force your application to send requests to other applications.
Broken Access Control
The 5th vulnerability of the OWASP TOP 10 2017 is unauthorized access to functions and data – Broken Access Control. It can be done by using the regular user’s account to access the privileges of the admin account. That way, for example, the attacker could be able to access the medical documents of all clients registered in the application. Broken Access Control remains one of the most prevalent issues in the OWASP TOP 10 lists.
Security Misconfiguration
Misconfigured security measures are very common in web applications. Some of them include:
- poorly configured cloud permission settings (e.g. S3 buckets),
- default and test accounts with generic passwords that found their way to the production environment,
- too detailed error messages,
- no HTTP Security headers.
This vulnerability is often just a prelude to many of the other, even more, serious ones, such as XXE or command injections.
Cross-site Scripting (XSS)
One of the most popular and talked about vulnerabilities, widely known even outside of the cybersecurity crowd. This time, it ranked 7th and I believe that it’s going to return in the 2020 edition as well. I still find this vulnerability often in the applications I test, despite all the security measures employed in modern-day frameworks. XSS involves injecting malicious scripts and executing them on the computer of the victim.
Insecure Deserialization
The official definition describes this vulnerability as a situation in which “untrusted data is used to abuse the logic of an application”. In other words, the app replaces the proper set of data with malicious code, allowing for DoS, RCE and other types of attacks. This code leverages the legitimate serialization and deserialization process recognized by your web app.
Using Components with Known Vulnerabilities
Ensuring that your libraries, frameworks and components are up-to-date goes a long way in making your app more secure. Otherwise, the practice ufo using components with known vulnerabilities may make your app prone to a variety of problems typically caused by outdated software. Therefore, make sure that your content management system, analytics software and libraries are all regularly updated, even after they are released to the production environment!
Insufficient Logging and Monitoring
The last position is not really a typical vulnerability, but an example of oversight on the part of cybersecurity specialists. It has to do with insufficient logging and monitoring of error and inadequate reaction to various incidents. It may result in a variety of attacks, damages and exploits.
To combat such threats, you should definitely store information such as HTTP code statuses, timestamps, API endpoint users, page locations or IP addresses in your logs. Of course, they need to be stored in a secure location, as they contain a lot of sensitive information.
You should also pay special attention to suspicious actions, such as multiple login attempts, script injection attempts, requests made by unusual IPs and locations, the usage of automated tools and more. Other than monitoring and logging, you should also actually act on your findings, for example by blocking users that display this suspicious behavior.
Other security vulnerabilities
It’s important to remember that these ten vulnerabilities by OWASP TOP 10 are just some of the threats found and tackled by pentersters and cybersecurity specialists. There are many other more or less popular forms of attacks such as:
- buffer overflow,
- memory leak,
- process control vulnerabilities,
- heartbleed bug,
- CRFL injection,
- SSRF injection,
- path Traversal,
- clickjacking,
- HTTP Host Header attacks,
- and more!
Software security trends are just one of the many areas of software development we follow. Check out this article to learn more about testing trends.
OWASP TOP 10 2020
As of today, the 2020 ranking that covers the years 2017-2020 is still yet to be released. In the meantime, I can try to predict some of its content based on my own experience in this field.
Cross-Site Scripting
In my opinion, XSS will most definitely remain on the list (perhaps somewhat lower than in the 2017 edition).
Injections
Aside from XSS, all kinds of injections (SQLi, NoSQLi, Command Injection) should remain in the ranking as they still constitute a very real in today’s world of cybersecurity.
GraphQL
I would also be surprised if GraphQL didn’t make the list. This data query language for APIs has become very popular in the past several months.
Server-Side Request Forgery
Cloud solutions are becoming more and more popular each day. It makes sense for more cloud-related threats to appear in the OWASP TOP 10. This may include Server-Side Request Forgery – a vulnerability that originally showed up in 2002 and recently came back like a boomerang. Initially, it had a rather low-to-medium priority. Today, it’s high or even critical. Back in 2019, Paige Thompson made a point of it when he managed to steal data from 106 million consumer loan applications.
Unpatched Libraries
This one may seem comparatively trivial, but it is serious. In today’s software development, there are simply so many things to do that keeping libraries up-to-date is not often prioritized. When the client does not take proper care of it, an audit of libraries and frameworks may be necessary.
OAuth 2.0
It’s an authorization framework that makes it possible for websites and applications to request limited access to the user account or another application. It’s being replaced by OAuth 2.0 – a new standard written from scratch. It’s getting popular, but since it’s so new, it’s also more vulnerable when it comes to errors during the implementation process. Therefore, it may show up on the OWASP TOP 10 2020 list, either as a standalone technology or as part of authentication vulnerabilities.
HTTP/2 related vulnerabilities
Attacks related to the latest HTTP/2 protocol are also a possibility. These usually involve setting up a queue of requests that exhaust server resources – Denial of Service. Fortunately, this vulnerability does not enable the attacker to steal any information or modify data.
Want even more software development trends?
OWASP TOP 10 2020 update
After months upon months of waiting, the updated version of the OWASP TOP 10 ranking is finally here! At this moment, it’s still an early version and some minor changes may still occur. However, the vulnerabilities themselves should not change. Let’s review them!
Big changes – that’s how I could sum up the new version of the most popular (but not necessarily the deadliest) vulnerabilities when compared to the previous version.
The full list is as follows:
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging and Monitoring Failures
- Server-Side Request Forgery (SSRF)
In this year’s ranking, The OWASP community decided for the first time to break down almost all the vulnerabilities into general groups/classes (with the exception of SSRF). Some classes appeared before (e.g. Injection), some are completely new and include vulnerabilities that have shown up before. For example, Cross-Site Scripting (XSS) was included in the Injection class, while XML External Entities (XXE) is now part of Security Misconfiguration.
It might make comparing the versions a bit harder. But overall, I like the change. I can imagine that some popular vulnerabilities might have been kept out of the ranking in the past by a couple of votes, even though they should have been included.
Let’s review the new list quickly:
1. Broken Access Control
The new ranking’s winner moved from 5th place when compared to the previous version. This vulnerability is all about unauthorized access to functions and data.
2. Cryptographic Failures
A new vulnerability, which has caused quite a lot of controversy in the industry recently. Cryptographic failures can be quite dangerous. But are they popular? I’m not so sure.

3. Injection
Downgraded from the 1st spot. It includes vulnerabilities such as XSS, SQL Injection, and others.
4. Insecure Design
Another vulnerability that proves that the conversation about security should start at the very beginning of a project (shift left security; a similar approach is used in QA – see shift left testing). It includes project- and architecture-related flaws and underlines the necessity of threat modelling, creating secure design patterns, and reference architectures. All of these issues are often downplayed. How to prevent it?
- Establish and use a secure development lifecycle.
- establish and use a library of secure design patterns or paved road ready to use components.
- Use threat modeling for critical authentication.
- Access control, business logic, and key flows.
- Write unit and integration tests to validate that all critical flows are resistant to the threat model.
5. Security Misconfiguration
Moved one spot up. You can read more about it in my commentary to the 2017 version.
6.Vulnerable and Outdated Components
It includes vulnerabilities such as outdated libraries, unsupported frameworks, no repository scanning, outdated components in the production environment, or no compatibility testing.
7. Identification and Authentication Failures
Previously referred to as Broken Authentication. You can read about it above.
8. Software and Data Integrity Failures
Another new vulnerability class. It revolves around software updates, critical data and CI/CD pipelines, deserialization of untrusted data, including functionality from untrusted control sphere or downloading code without integrity check.
9. Security Logging and Monitoring Failures
Another vulnerability from the previous ranking that moved up a spot.
10. Server-Side Request Forgery (SSRF)
This subject returned because of the increase in the popularity of microservices and cloud solutions. It appeared for the first time in 2002 and remained forgotten for years. It will most likely be included in a more general vulnerability class later.
How did our OWASP predictions turn out?
I guessed 4 out of our 7 OWASP predictions.
Predicted OWASP vulnerabilities
- XSS – it was moved into a more general class, but it’s still an extremely important vulnerability to watch out for.
- SSRF – it made it onto the new list!
- Unpatched Library – it showed up as Vulnerables and Outdated Components.
- Injections – remained in the new ranking.
Missed OWASP vulnerabilities
- OAuth – this time, this vulnerability related to OAuth did not show up. Still, it is something worth looking into.
- HTTP/2 – sadly, it’s missing in the new ranking.
- GraphQL – this data query language for APIs is now very popular and I am a bit surprised that it was not included as part of any of the vulnerability classes. But I do suspect that it might be later added to the OWASP TOP 10 API list.

And that’s it for the 2020 OWASP predictions!
OWASP TOP 10 – summary
There are many web application vulnerabilities and it’s difficult to determine the most popular ones. However, the OWASP ranking gives you a good sense of what is currently going on in the world of web security. I’m looking forward to covering future editions! Looking for an update? Check out the articles from 2022 – API security top 10 ,and security threats spotted by QA engineers!
And if you need a team that does follow all the best practices to stay clear of all the security threats and vulnerabilities…
…contact The Software House!

