24 August 2021
Personal cybersecurity best practices – checklist

In today’s world, where all of us moved to the internet in order to escape the pandemic, it all happened very quickly. We’ve changed our habits, so we don’t need to make unnecessary personal contact. But have we spent even a fraction of that time thinking about our personal cybersecurity? Introducing the Personal Cybersecurity Checklist!
Today, our everyday routine has largely moved to cyberspace. We chat with people using cameras. We shop for things online. We’re having fun integrating online and playing games. All of this in order to protect ourselves.
In light of that, it may be a decent idea to brush up on some good-to-have manners when surfing on the web (but not only!). These areas include:
- Human Factor
- VPN
- 2FA
- Phone
- SIM Card
- Computer
- Passwords
- Credit Cards
- Web
- Social Media
- GPS/Geotagging
- Phishing
- Chats
- Backups
- Updates
Security is clearly a very broad area to dive in, even when it comes to everyday personal life. Let’s discuss each point on it’s own.
The human factor – a.k.a. who is the bad guy?
While in real life, it’s very easy for us to verify our peers. On the internet, we have to believe that their nickname and photo are the same person behind the keyboard. But it’s not always the case. We’re hearing more and more often about people impersonating others in order to trick into some kind of scam – this type of crime almost doubled in the first half of 2020 alone (up to 84% increase).
“Bad guys” know that we’re less cautious under pressure of time and emotions. When they try to convince us (by pretending to be our close relatives or friends) to send them some money or click some links, they claim that this is very urgent or that they are in danger. While these things of course can happen for real, we always should verify the other side, even by simply calling them on the phone or asking them to do it. They lost their phone? We can fall back to asking some private questions that only both of you know.
Either way, using common sense and limited trust when contacting your close ones is imperative. But this isn’t limited to friends on Facebook. Scammers can reach people directly via phone or mailbox (both real and electronic one). Common examples are bank workers calling and asking things like the mother’s maiden name or worse, the credit card PIN. These should raise suspicions and are a good reason to disconnect and phone the bank directly to ask about the worker’s identity and their questions (the worker should of course present their identity over the phone).
Another widely spread scam is based on unpaid invoices. We may panic that we will lose power and want to pay it off as quickly as possible. But there’s a slight doubt – why would it go to the mailbox? It’s best to contact the other side and verify it, or try to search on the internet for similar cases. It may turn out that this is actually a scam and people already are reporting this.
LESSON: it’s vital to verify peers and emails using an alternative contact channel when things get suspicious.
VPN
VPN (Virtual Private Network) is probably something you’ve already heard of since there are a lot of commercials coming from providers to use their solution. Even web browsers offer built-in VPNs (Opera). The basic idea of VPN is to encrypt and tunnel your traffic to a desired location (webpage, server) so nobody can hijack or eavesdrop it in the middle. The other end won’t know the original source of the traffic since it came from the VPN server and not your computer.
This means that if we connect to a VPN server in America, Netflix will think we live there and offer us local american shows. Another useful purpose of VPN is to avoid censorship in countries that like to spy on users or block some kind of traffic (if it’s encrypted they don’t know what exactly is being sent).
However, this solution doesn’t provide complete anonymity. Of course, it will be harder to track a VPN user down. Providers say they don’t keep logs from connections. But one can’t always trust them as they have to comply with local law and jurisdiction. They also are often targets of attacks, since hijacking a VPN server means the attacker can decrypt all the traffic going through and that might include sensitive data.
If one wants to have a VPN provider that is trustworthy, there’s a tool called Algo that can help set up a VPN very quickly using some VPS (virtual server) on cloud providers such as AWS, Google or Digital Ocean. That way, it’s possible to ensure what logs are being kept on the server.
LESSON: using VPN to improve your privacy is a good idea, but it does not guarantee anonymity!
2-factor authentication
Password leaks happen very often, if not every day. That’s why it’s not enough to have a combination of two strings, where only one of them is known to us. We need another factor in order to prove our identity to the service that we log in. This is where the second factor comes in. This is usually OTP (one-time-password) that is rotated and valid for a short period of time (to avoid stealing that code and reusing it).
Another form could be biometric (think fingerprint or faceprint), but these are costly and hard to integrate with web services. They are used mostly on physical barriers such as doors in a bank or so. YubiKeys are also gaining popularity. They are becoming widely adopted by giants such as Microsoft, Apple or Facebook as another 2FA solution users can use. In that case, apart from the usual username and password, our YubiKey (a physical device) is a second factor that can vouch for us. However, losing it will lock us out of our accounts so it’s a good practice to have two of these so one stays in your drawer as a backup.
Using 2FA greatly increases our security, but it’s not phishing-proof. We still can be tricked into giving our one-time code to the attacker via a phishing site. Then, they will log in on our behalf to proceed with their attack. A very good example of why 2FA is not 100% secure is the recent breach into Electronic Arts. Someone stole credentials from one of the workers, impersonated him on Slack and asked support to disable 2FA, because he “lost his phone” (second factor). That allowed for stealing a lot of data from the company by using social engineering and human factor weakness.
LESSON: it’s worth using 2FA whenever viable.

Phone
Our phone probably knows more about us than anyone else. Our message history, location, where we’ve been, things we bought and so on… We wouldn’t hand in all of the information to a stranger, would we?
That’s why we should take care of the privacy and security settings of our phone. Not so long ago, there were a lot of applications that abused permissions and tracked way too many things that they should. This led to unintentional leak of personal information, which then were used to target advertisements and attacks toward unaware users. Luckily, this has been improved by basic operating systems vendors like Google and Apple. Browsers also follow this trend. It seems like more and more people are becoming aware of this practice.
But that’s not all, our phone has other factors apart from applications that we should take care of. First of all, our first protection is either the PIN code, face recognition, fingerprints, voice activation or pattern code. Apparently, PIN or password is actually the best way to protect a phone, assuming the PIN code is at least 6 digits long. Patterns are considered a no-no since most people use repeating patterns and it’s easy to crack.
Biometric security measures are known to fall to attacks, same with too short PIN codes. So while it’s very convenient to use biometric, it’s vital to know that someone can force us to unlock our phone by using our fingerprints or face. If we wish to disable biometric validation, we force-do this by pressing the lock button on the side of the iPhone a few times or through a combination of side button plus volume button. This feature has also been introduced to Android, but it’s usage varies depending on manufacturer. Another unwanted feature that many may not be aware of is “important locations” (iOS feature) or Google Location History (Android). It’s worth checking if our phone does track us in these settings (iOS):
Settings -> Privacy -> Location Services -> System -> Services -> Significant Locations
Settings -> Privacy -> Advanced -> Location History
LESSON: it’s a good idea to get to know our phone better, in particular review security settings and location tracking.
SIM card
It’s been years since the first attacks were spotted using clones of SIM cards, yet this technique has reached its popularity peak lately (2019-2020). Here’s just one of the stories that was quite famous around the media – someone stole over 400.000 PLN from a woman using this very technique.
Sounds scary? It should be. First signal of attack is losing mobile network connectivity out of the blue. If this isn’t a regional outage, we should try to contact the mobile operator as soon as possible. How can we protect ourselves from this attack? Unfortunately, we can’t, since mostly our mobile operator is the one who fails to follow the verification procedure and allows the attacker to obtain our SIM card clone.
Luckily, mobile banking has gone forward with authorising transactions, and we’re no longer obligated to use SMS to confirm our bank operations. Some banks even withdrew that method, which is a very good move.
What we should use instead is our mobile banking application and its push notifications. A second factor is enabling transaction notifications. We want them to see if our credit card was charged and if we expected that. This and regular bank account history overview will go a long way to protect our finances. As for extra-layer security, we could have a separate number for banking only, but this would be quite troublesome day-to-day. As a fun fact, some providers in America allow people to use something like a “mobile carrier PIN”. Each change on the account (e.g. granting a duplicate SIM card) requires giving a special PIN code, which is only known to the customer of course.
LESSON: using mobile authorisation for mobile banking and avoiding SMS authorisation in any service where possible.
Personal computer (PC)
This one sounds easy, right? We should just remember to have a password on our computer and lock it when we leave. There’s more to that!
Since GDPR came out, we should be even more sensitive to what we expose on our screen. Especially if we have to work in some public place, coffee shop, train, lecture room, it’s important to remember that someone can be watching behind our shoulders. The best way is to avoid working with sensitive data in public places, but when we have to, we could use a privacy screen protector for our display. It hides everything from the view, unless someone is right in front of it under the right angle. Another thing that we should do is encrypt our hard drive. If our computer was ever stolen or sold, that makes retrieving data on that disk virtually impossible. We don’t want someone to leak information from our computer, either of personal or business kind.
LESSON: avoiding working with confidential data in public places and using privacy screen protectors if so, encrypting our hard drive.
Passwords
Our password will eventually leak. It’s only a matter of time and we can’t avoid it completely. What we can do is stop using one password for everything. Even if it’s very complicated, someday it will be exposed and all our accounts will be overtaken. 2FA won’t help if you become the victim of a phishing attack. In fact, we can always check if our account / password has been leaked on this site. We can also sign up for notifications if they ever find our email in new leaks.
But it’s all small steps until we start using a password manager. This super helpful application will secure all our passwords to hundreds of websites in a secure vault, which is protected by only one password (that should be complex and secure in and of itself). Then, when trying to log in somewhere else, we simply copy the password from it (a browser addon can also do it for us and auto-fill it) and log in to the website. What’s more awesome, a password manager can generate a complex password for us and save it in a vault. We don’t even need to memorise that password, because it’s safely stored there. All we need is one master password. A couple password managers that are widely recommended and adopted:
Are there some others worth mentioning? Any recommendations appreciated!
Fun fact: Google Mail allows for using our email in the form of “[email protected]”. Emails will still come to our basic email “[email protected]”. It means that if we register to Netflix as [email protected] and we see the credentials to myemail+netflix leaked, then we know for sure the source of that leak…
LESSON: using a Password Manager really pays off
Credit cards
This is something we use on a daily basis, yet all we care about is not to lose it or lend it to someone else. If we ever lose it, we should call the bank. And that’s it for most of us. But there are actually a lot more things that we should be concerned about.
First, having more than one card is actually not a bad idea. There are a couple of reasons for that. What if we needed to pay for something and the bank extended its maintenance? A second card from another bank to the rescue!
Another example – what if our credit card data was leaked by some online shop we used? We can designate a special card for online payments only and send just enough money to it to cover our subscriptions such as Netflix or Spotify plus some change for food ordering! Worst case? We lose our monthly subscription payments. And the habit of not keeping too much money for online spending will surely save some pennies! If we ever need it, we can transfer money to it and buy something. For urgent cases, we can always use express transfer. Going on holiday? Let’s take one card and leave the other somewhere safe. Drawbacks? Monthly payments for a credit card, but with the right spendings and good bank we can avoid it!
Now, let’s dive into the digital world. First and foremost: SETTING LIMITS! If we happen to be a victim of some attack, this can help us save ourselves from waking up to an empty account! We should do this for all possible limits we can in our bank, including online transfers, express payments, credit card, or contactless payments. Usually we don’t need high limits for day-to-day use. If we plan to buy something expensive, we have to remember about increasing that limit. Some banks allow for raising that limit for a period of time, so we don’t forget to set it back to normal values, since that happens automatically.
Another good habit to have is reviewing our account history on a regular basis. We might find some old, unused subscription that we pay for… let’s cancel it and save some money! Old-but-gold attack that was on the rise some time ago involved using devices called “skimmers”. What is it? It looks like this:

This is put on the card slot as an extra layer. It scans our credit card and, together with a small camera installed to watch us type PIN code, they clone the card and take out the money… unless we set some limits! 💪 And last bit of advice – the chargeback. When we pay for some wares and don’t receive what we expected, we have rights to get a refund, even up to 120 days after the transaction had taken place. So it’s quite safe to pay with a credit card, assuming we can prove to our bank we didn’t order that thing.

LESSON: setting limits on our bank account is the way to go.
Web
The browser
Surfing all day long on the web, we all know something about it, don’t we? And do we know in just how many ways sites are tracking us? What do they really know about us based on the links we click? It’s hard to tell…
Luckily, some browser vendors started implementing methods to stop random sites from tracking us. Some good examples are Brave, Firefox or TOR Browser (an exotic one!). But these functionalities have been around for a long time, provided by many trusted and known browser add-ons (they can also tell us who tries to track us, you’d be surprised!). These are:
- AdBlock (used to block YouTube ads),
- Ghostery,
- uBlock,
- Facebook Container.
We might want to take a look at our browser addons repository and add them to the collection.
Domain Name System (DNS)
Another issue has to do with DNS. It translates human-friendly names to IP addresses (because no one would remember those), and that way, DNS providers can collect a lot of information on us, because every site we visit needs to check what IP address it has via DNS. Very widely known DNS servers come from Google of course! These are 8.8.8.8 and 8.8.4.4. If we wish to stop Google at least a bit from tracking us, we should change these to something more private like 1.1.1.1 (CloudFlare) / 9.9.9.9 (Quad9) (it’s not that hard, promise! It’s a good idea to search for guidelines on how to do it on our specific system).
Transmitting documents on the web is another important issue. Whenever someone asks us to scan our passport or ID, we should be aware that an electronic copy can be abused to steal our identity. In order to protect ourselves from it, we can use a watermark on our documents that clearly says “copy made for X bank on day 10.10.2021 for Y purpose”. This way, if anyone ever gets their hands on these scanned documents, there is a very low chance they’ll be able to do anything bad with it.
The search engine
For the last piece of advice on how to improve your security standing on the web, it’s worth looking for Google alternatives in terms of privacy. This may be the DuckDuckGo search engine or the ProtonMail/FastMail/Tutanota mail service. As a fun fact, some brave man made an experiment to cut off tech giants from their day-to-day life. Quoting some very surprising numbers:
- 2 million data packets were sent out to the internet and more than half of them (60 percent) went to the tech giants.
- The number of IP addresses controlled by giants was incredible with 23 million, 21 million and 17 million owned by Amazon, Microsoft and Apple respectively.

LESSON: On the internet you are the prey and nothing is really for free!
Learn more about security testing in web applications as well – check out this great article from my colleague.
GPS & Geotagging
For some reason, a lot of applications try to track our location to “serve you best offers, while you are near!”. The world has gone forward and Android & iOS is telling us about it and restricting what applications have access to our data.
What some may not be aware of is a feature called geotagging. It’s supposed to be turned off now by default, but back then it was widely used by unsuspecting users. Basically, when one took a photo, its metadata automatically included GPS coordinates of where this photo was taken. It’s a good idea to check for the option “disable geotagging” in our mobile phone operating system. As a fun fact, a few years ago the prime minister of Poland’s website was hacked. The “Hacker” put a photo of himself on the website. It turned out it contained the metadata of his location. It’s easy to guess what happened next…

Phishing
This term has started to break into the mainstream media only lately, so many people may not have heard of it. However, its history is much longer. At its most basic, it involves tricking someone into some actions that often lead to very bad consequences for the victim such as cleaning their bank account, or overtaking their account on social media. A classic example is tricking someone’s relatives into sending money to a scammer.
The human is often the weakest link in the chain, so attackers rely on psychological tricks to do what they want. They try to convince us that we are in danger or to the contrary – that we have just won the lottery. Or that we will lose access to our bank account if we don’t “change our password RIGHT NOW”. As with a lot of other things, we must start using our common sense. What is the chance that our uncle from Nigeria has just left a mountain of money for us? Does someone really want us to click into “OMG, amazing history, there’s your photo in there!”? And the link looks like “bbbc.uk/your-name-here-shocking-history“?
Well, let’s think twice before clicking it or verify it using a second channel like “Did you just send me this weird link?”. We often hear how attackers overtake social media accounts and trick our closest ones using their trust in us.
If we are ever in doubt, there are online tools like this one: where one puts a link and it says what it does. We may learn that it downloads some malware or redirects to a bad site. And to further educate ourselves, how to spot fake data, emails and so on, look up phishing quizzes!
LESSON: it’s important not to trust any link we get right from the start. Use common sense and freely available resources to ensure it’s trustworthy.
Chats
We chat with people everyday on Facebook, Slack, Google Meet, Teams, Skype… and how often do we think about who can read these messages? Or how confidential they are? If we really need to keep our conversations private, we should take a closer look into messengers that are end-to-end encrypted.
The most popular solution on the market is currently Signal. Its good reputation has caused it to be banned in Russia & China, due to the fact they refused to give keys to un-encrypt user messages. However, Russia lifted the ban because in reality it wasn’t really effective and there were workarounds to use Signal still. Some also suggest Wire or Threema. Another popular one back in the day is Telegram. While it has a good reputation, it’s encryption functionality is disabled by default and requires enabling it for each conversation separately, which is a huge disadvantage. Also, when we decide to start using one of the proposed solutions, the biggest problem each time will be convincing our friends to follow our example…
LESSON: using trusted & secure chat solutions can go a long way to help you with cybersecurity
Backups
People fall into two categories, they either make backups or they think they do… how come? We are often told to “make backups!” but how often are we told to “test backups!”? It’s important to do that if we don’t want to wake to:
- external drive failure,
- corrupted data on all of your photos,
- a virus encrypted your data on a USB-connected disk (but this was my backup!).
There’s a golden rule for backups, it’s called “3-2-1” and stands for:
- three copies of your data,
- two different media where they are stored,
- one volume should be offline stored.
Simple example: we have our (1st copy) PC, we upload our files to (2nd copy) Dropbox or Google Drive, yet at same time, we backup these files to external USB disk (3rd copy – offline), which we disconnect right after taking backup. If for some reason our computer broke, we can recover from Google Drive. Virus removed all of our files in the cloud? Let’s restore from the USB disk (bonus points, if we keep it in a different place to avoid theft or fire). As for popular backup software, it’s worth it to check out:
- Windows Veeam – it has free, personal edition for use,
- MacOS – Time Machine, built-in software,
- Online Backup – Backblaze (Windows, Linux, MacOS).
Any other alternatives worth mentioning are appreciated!
Updates
One of the most important rules to follow & easiest to execute. And yet a lot of people skip it… Why is it so important? It has to do with the term 0-day. That means that outside there’s a vulnerability that hasn’t been yet discovered & patched and someone may actually use it to take over control over our devices or start spying on us. Looking at number of total vulnerabilities below, numbers are rising each year, which means there’s more and more 0-days.
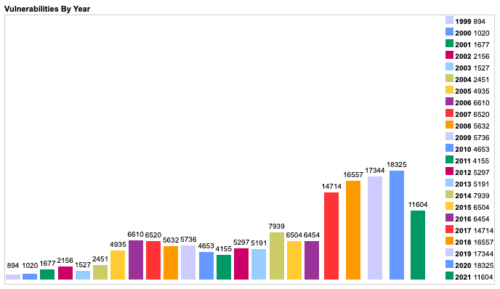
Basically, every device and application that we use needs updates.One of the most targeted attack vectors is the web browser. We should patch that one up as soon as possible, although most modern browsers patch themselves up on startup.
In the case of our operating systems, while it’s also very important, we might want to check its stability first. There were quite a few problems with updates, and they still continue to appear. That’s why it’s worth looking up terms such as “iOS X.X issues” in the browser before proceeding with the update. Backups can save us here if we do them properly and test them as pointed out in the previous part.
LESSON: doing updates is good, but it’s important to make sure they won’t cause any trouble
Summary & the Personal Cybersecurity Checklist
Okay, this has been a long article! Let’s wrap things up with a nice little infographic… (it may be a good idea to download or print it)
… and a good old piece of wisdom!

You want to get serious not only about your personal cybersecurity, but also the security of your IT project?
It might be a good idea to contact our developers. We can almost surely find a way to help you.


Social media
What goes on the Internet stays there. We all may have heard that, but there’s more. Whatever becomes digital can also leak to the Internet. How? There was a noisy story about it, in which a woman’s photos were leaked to the internet during a service repair… Another example is iCloud and its great feature of backuping our photos for future sharing among our private network of contacts! Well, a lot of celebrities thought so too.
While social media has expanded a lot in recent years and we have a lot of possibilities to socialise with other people, it’s not for free. In that case, we and our data are the product. First of all, we should limit who can see our private information that could be used for a potential phishing attack or, surprisingly, by a bank, which may decide to refuse to give us credit because our online profile says we’re spending too much money.
LESSON: putting everything into the digital world comes with risks. It’s a good idea to analyze our social media privacy settings.